How to Use the Where-Used and Assigned From Features
|
Video: Summary Permissions and Calculations (20:52) The information provided by the Where-Used features in Easy Security is useful for providing more in-depth information on where and how an object, permission set or company is used in security. Three Where-Used features exist: Object Where-Used, Permission Set Where-Used and Company Where-Used. Each Where-Used feature provides a great deal of information. There is also an "Assigned From" feature that provides information about which Permission Set provided a Login permission to a specific object. The Object Where-Used feature provides information as to which Permission Sets include access to a specific object. To use the Object Where-Used feature: 1) Open Object Where-Used from the Logins and Permissions menu. 2) Set the Object Type field to TableData and set the Object ID: to 17 for the G/L Entry table. 3) Our example shows that TableData 17, the G/L Entry table, appears in 69 Permission Sets, the TableData has 37 relations and the Used as Relations field shows 90. It was included in 52 Recording Permissions and it was included 19 times in Builder Permissions. You can drill down on the numbers to see supporting data about each piece of information. 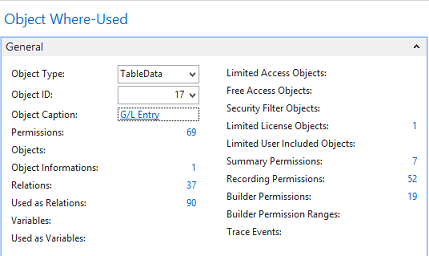 4) The Object Where-Used feature has 4 Pages: General, Field Level and Data Security, Restore Point and Live. Field Level and Data Security cannot be set up for TableData, so there is no information available on that Page. However; information is available on the Restore Point and Live Pages as can be seen in the screenshot below. 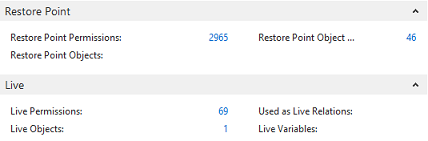 5) Change the Object Type: filter to Table and the information changes. The G/L Entry Table appears in 1 Permission Set, the Table has 37 relations. It has 14 Variables. You can drill down on the numbers to see additional information about each piece of data. For example, of the 14 variables, 2 are Global and the other 12 are Procedure Variables. The Table is used as a Variable 137 times. It was included in 66 Recordings and it was used 1 time in the Builder Permissions. You can drill down on the numbers to see supporting data about each piece of information. 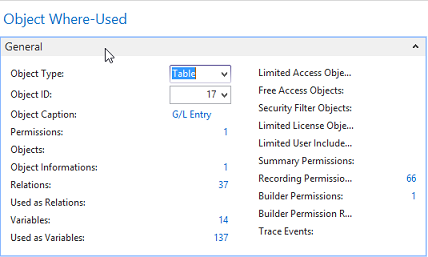 Table 17 is used in Field Level and Data Security, Restore Points and in Live. Drill down on the numbers to see supporting data about each piece of information. 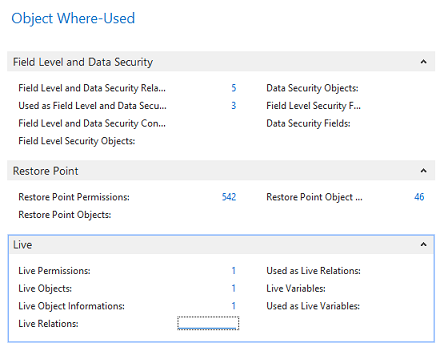 6) Open Permission Set Where-Used from the Logins and Permissions menu. 7) Select the BASIC Permission Set ID. This is a good Permission Set to review since most users are assigned this Permission Set. The Permission Set Where-Used feature shows various types of information about the selected Permission Set. Notice that the selected Permission Set is assigned to 7 User Access Controls, is included in 4 Permission Group Lines and is included in 23 Restore Points, etc. You can drill down on the numbers to see supporting data about each piece of information. 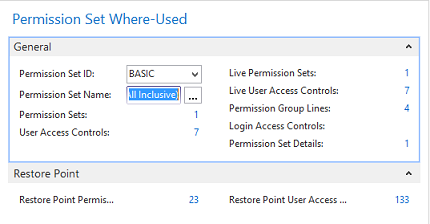 8) The same type of information is provided by the Company Where-used feature as was provided by the Permission Set Where-used feature. Just select the Company of your choosing in the Company Name field. You can drill down on the numbers to see supporting data about each piece of information. 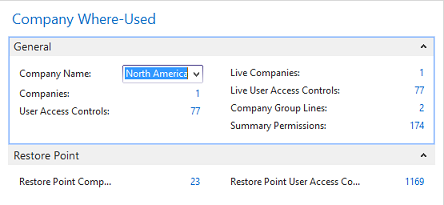 Assigned From Feature: Use the Assigned From feature to determine which Permission Set provides permission to a specific object. This is a very useful tool for troubleshooting security. 1) From a Login Card or the Logins list page, click on the Summary Permissions Action in the ribbon to open the View - Summary Permissions page. 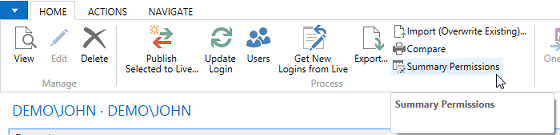 2) In our example, we want to know which Permission Set(s) provided John with access to the G/L Entry Tabledata 17. Select the line with TableData 17 and activate the Assigned From Action. 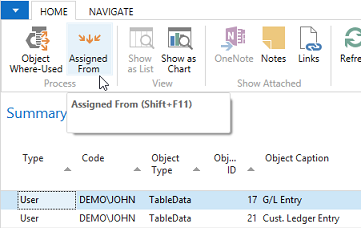 3) The results show that John received permissions to TableData 17 from 4 Permission Sets that are included in 2 Permission Groups. It displays the level of permissions provided by each Permission Set and shows that he has this access in only one Company. 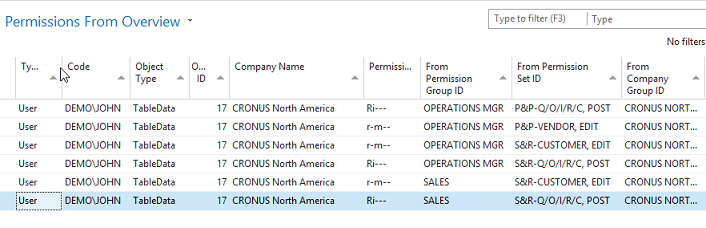
|
|
Like  Don't Like
Don't Like 
© 2024 Mergetool.com. All rights reserved. 
|
Related resources
Download software from Mergetool.com
